A Jenkins plugin that allows external systems to provide global credentials to Jenkins via external incoming webhook via HTTP POST requests protected by a Bearer token authentication.
This enables dynamic credential update from external systems (that can execute webhooks) or infrastructure automation tools when pull model is not possible.
If you are not clear about the next use case, you probably want to take a look at following plugins instead
- Kubernetes Credentials Provider Plugin to fetch credentials from Kubernetes Secrets
- Vault Credentials Provider Plugin to fetch credentials from HashiCorp Vault
- Azure Key Vault Credentials Provider Plugin to fetch credentials from Azure Key Vault
- Bitwarden Credentials Provider Plugin to fetch credentials from Bitwarden
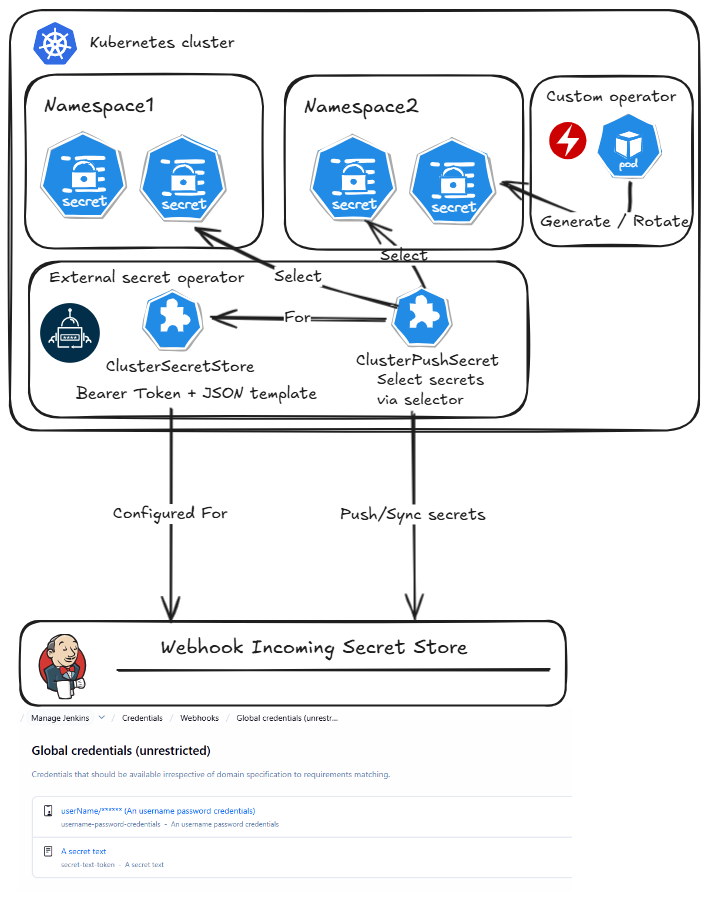
One of the use case is to have Kubernetes Secret in various Kubernetes clusters and namespaces and a Jenkins controller on a totally different infrastructure.
Having such credentials synchronized is critical specially when using short living token (like few minutes).
Using the External secret operator and PushSecret via Webhook Provider could rely on such API to keep the secret in sync.
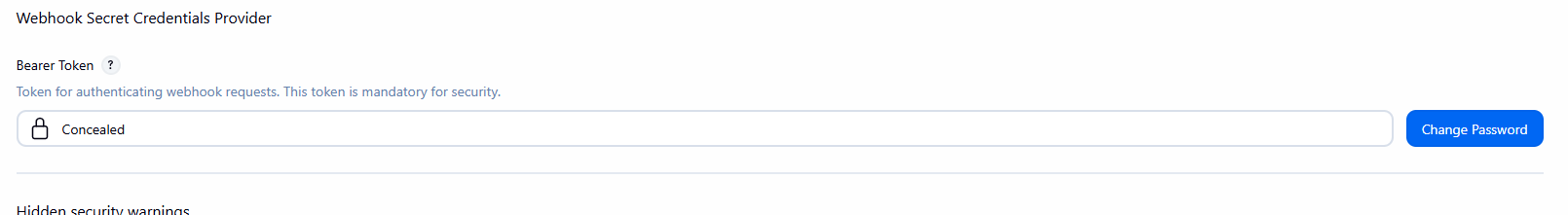
This plugin requires Bearer token authentication. All webhook requests must include a valid Bearer token.
- Navigate to Manage Jenkins > Security
- Find the Webhook Secret Credentials Provider section
- Set a strong Bearer token in the Bearer Token field
- Save the configuration
The plugin exposes a single webhook endpoint at:
POST {JENKINS_URL}/webhook-credentials/update
Authentication Required: All requests must include the Authorization header:
Authorization: Bearer <your-configured-token>
Send HTTP POST requests to the webhook endpoint with JSON payloads containing credential data and proper authentication.
All requests must include the Bearer token in the Authorization header.
http POST :8080/jenkins/webhook-credentials/update \
"Authorization:Bearer <your-token>" \
id=secret-text-token \
description="A secret text" \
type=secretText \
"secret[token]=1234"
http POST :8080/jenkins/webhook-credentials/update \
"Authorization:Bearer <your-token>" \
id=username-password-credentials \
description="An username password credentials" \
type=usernamePassword \
"secret[username]=userName" \
"secret[password]=password123"
http POST :8080/jenkins/webhook-credentials/update \
"Authorization:Bearer <your-token>" \
id=ssh-private-key-credentials \
description="An SSH private key credentials" \
type=basicSSHUserPrivateKey \
"secret[username]=sshUser" \
"secret[passphrase]=optionalPassphrase" \
"secret[privateKey]=-----BEGIN OPENSSH PRIVATE KEY-----
...-----END OPENSSH PRIVATE KEY-----"
data must be base64 encoded
http POST :8080/jenkins/webhook-credentials/update \
"Authorization:Bearer <your-token>" \
id=secret-file-credentials \
description="An secret file" \
type=secretFile \
"secret[filename]=foo.txt" \
"secret[data]=Zm9vLWJhci10ZXN0"
security:
webhookSecretStore:
token: "a very insecure token"
This plugin is licensed under the MIT License.