Jacked provides organizations with a comprehensive view of their applications to enable informed decision-making and improve security posture. Its primary purpose is to scan for vulnerabilities and guide mitigation efforts.
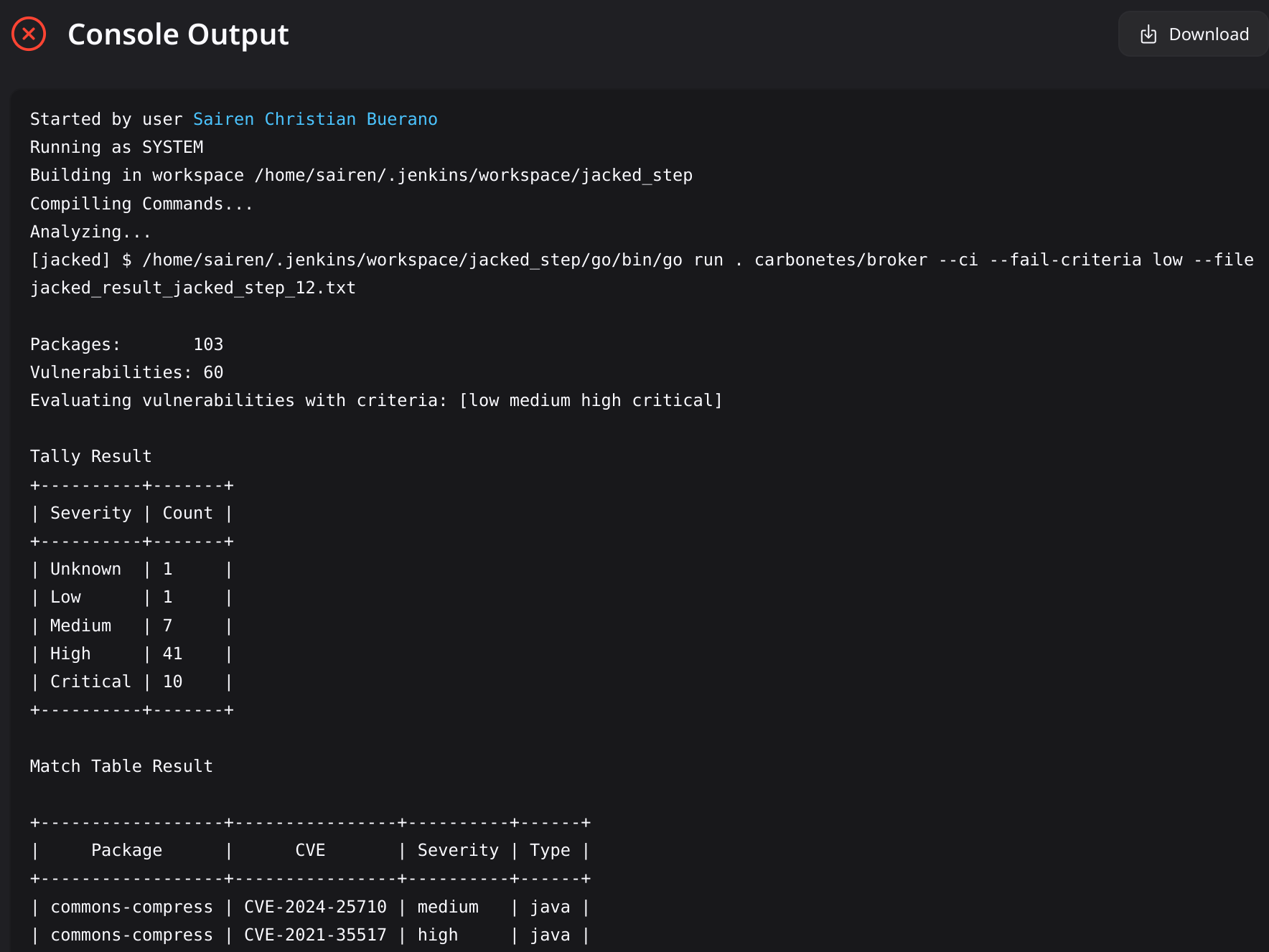
This Jenkins plugin scans a specified target and exposes its vulnerabilities.
This Jenkins plugin installs Jacked in the job’s workspace and runs a scan. It automatically sets up all required dependencies to run Jacked.
Description: Specified the input on scan field based on the selected scan type.
Option:
Image: Provide the image:tag.File System: Provide the target filesystem directory path.Tarball: Provide the target tarball file path.
Input: Image name, Directory path, or tar file path.
Description: Select a threshold that will fail the build when equal to or above the severity found in the results.
Option:
- Critical
- High
- Medium
- Low
- Negligible
- Unknown
Default value is false / unchecked.
Warning: If the value is checked, it will restrict the plugin from failing the build based on the analysis result.
pipeline {
agent any
stages {
stage('Jacked Scan') {
steps {
script {
jacked(
scanType: 'image', // Choose Scan Type: image, filesystem, or tarball.
scanName: 'ubuntu', // Input: image:tag, filesystem dir path, or tarball file path.
severityType: 'high', // Choose Fail Criteria Severity as a threshold.
skipFail: false, // Default as false. Always Build Success [Not recommended to set true!]
token: '' // Personal Access Token
)
}
}
}
}
}
Licensed under MIT, see LICENSE