⚡️ AI‑assisted DAST for CI/CD — launch scans, gate builds, and publish gorgeous reports.
🌐 Vines Cloud (production): https://vines.rosebird.org
Quick Navigation · What is Vines AI · AI & Reports · Install · Quick Start · Gates · KPI Chips · Pipeline · Examples · JCasC · Troubleshooting · Metadata · Maintainer
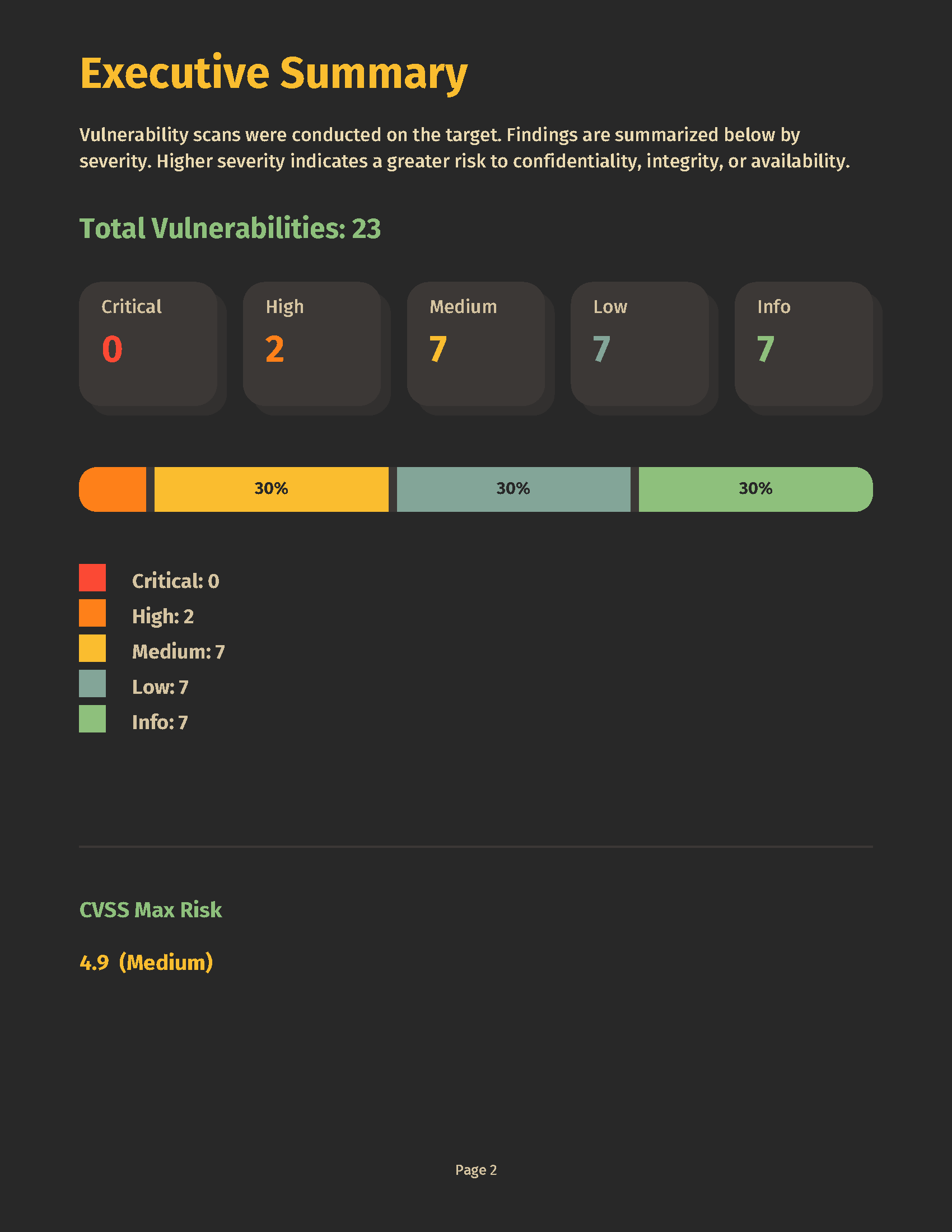
Vines AI is a modern, AI‑assisted Dynamic Application Security Testing (DAST) platform by Rocheston.
This Jenkins plugin integrates Vines directly into your pipelines so you can:
-
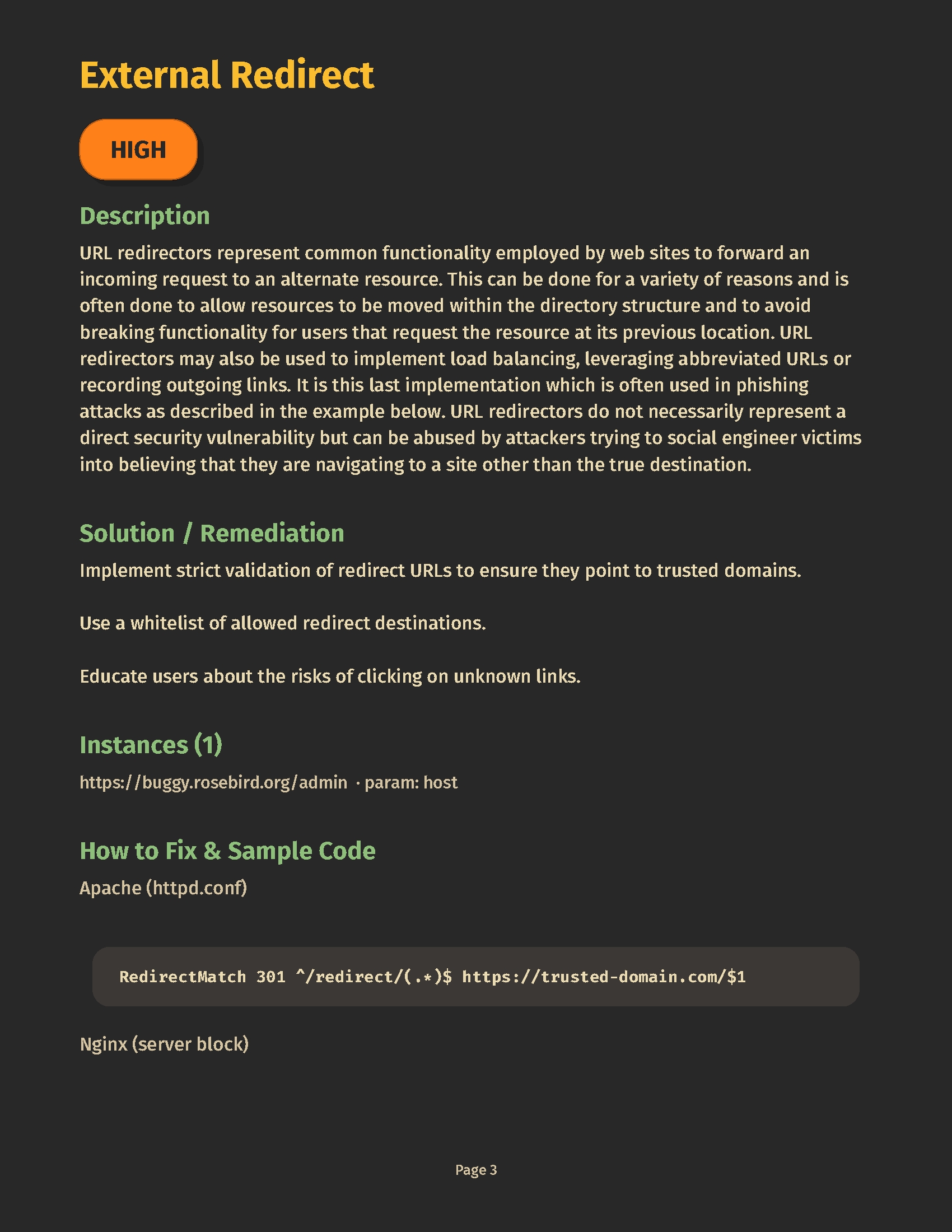
▶️ Trigger scans from jobs & pipelines againsthttps://vines.rosebird.org(or your on‑prem instance). - 🛡️ Enforce pass/fail Gates on risk (critical/high counts, maximum CVSS).
- 📊 Publish elegant summaries with KPI chips and deep links to the full report.
- 🔎 Run a Preflight probe (DNS/port/HTTP) before full scans to save build time.
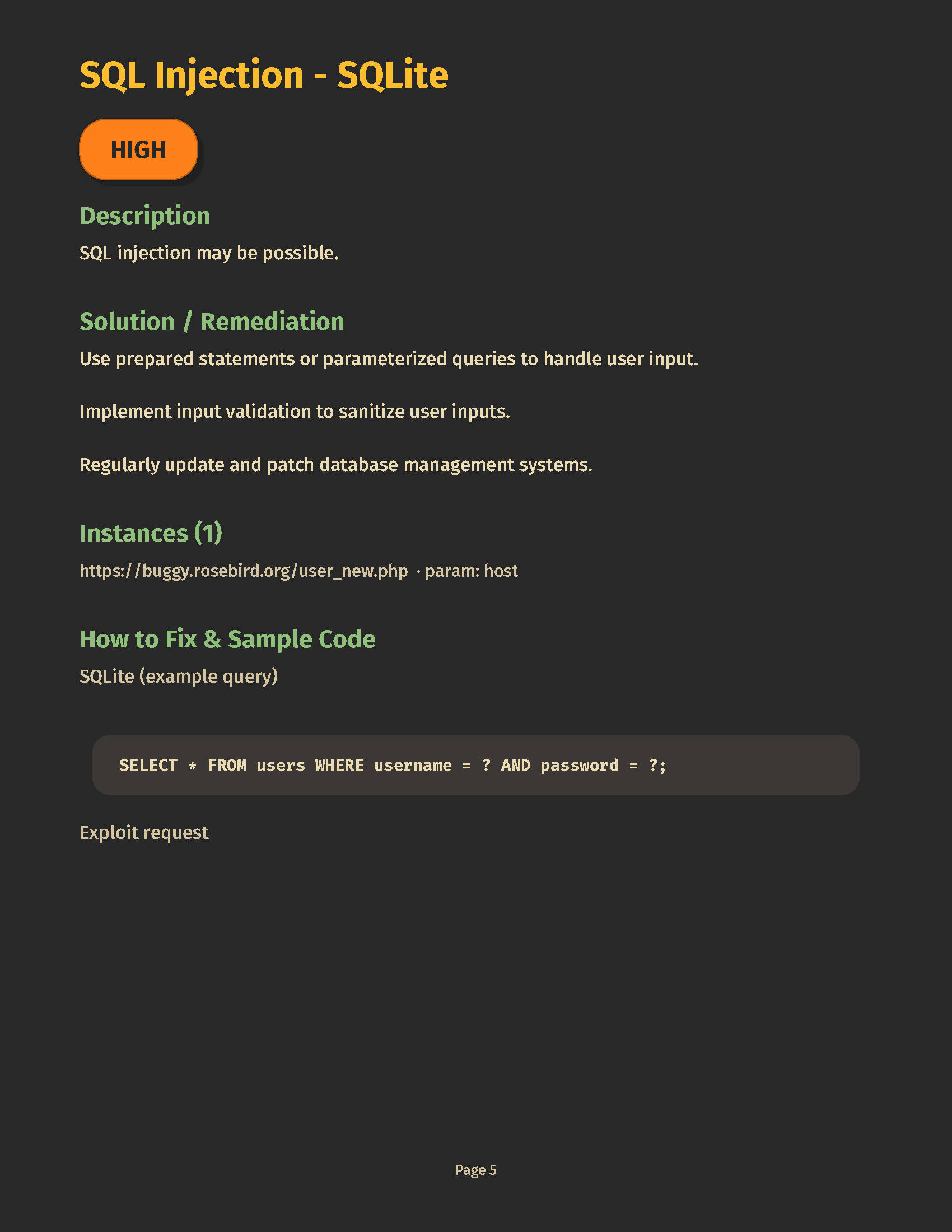
- Smart crawl + attack — adaptive exploration prioritizes real attack surfaces, trimming noise.
- AI triage — clusters similar findings, promotes likely true positives, de‑duplicates chatter.
- Explainer‑grade remediation — developer‑first guidance with code‑aware hints.
- Policy hints — recommends gate thresholds from historical risk patterns so you start sane.
- Manage Jenkins → Plugins → Available → search
vulnerability-vines-ai→ Install. - Create a Secret text credential with your Vines API token (ID example:
VINES_TOKEN). - Ensure your controller/agent can reach
https://vines.rosebird.org.
Manual (offline): upload HPI from Releases or from Jenkins repo:
https://repo.jenkins-ci.org/releases/io/jenkins/plugins/vulnerability-vines-ai/<VERSION>/vulnerability-vines-ai-<VERSION>.hpi
Minimum Jenkins: 2.479.3+
- Add build step Vulnerability Vines AI.
- Server URL:
https://vines.rosebird.org - Target URL:
https://app.example.com - Credentials:
VINES_TOKEN(Secret text) - (Optional) Enable Gates and adjust thresholds.
- Build → view KPIs, open the full report link.
pipeline {
agent any
stages {
stage('Vines Scan') {
steps {
vinesScan(
serverUrl: 'https://vines.rosebird.org',
targetUrl: 'https://app.example.com',
credentialsId: 'VINES_TOKEN'
)
}
}
}
}
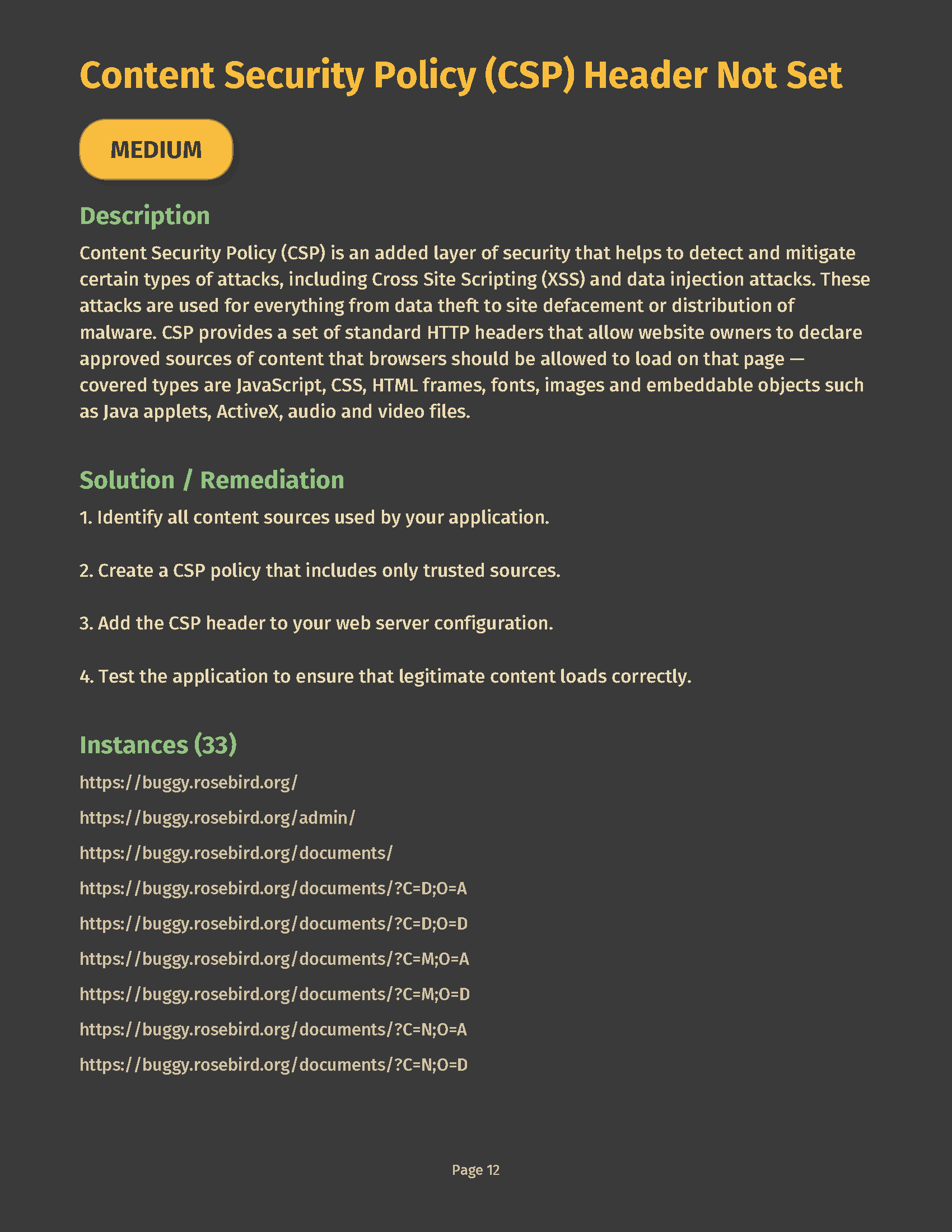
Block unsafe builds with policy thresholds:
| Gate | Meaning | Default |
|---|---|---|
failOnCritical |
Fail if ≥1 Critical | true |
failOnHigh |
Fail if ≥1 High | true |
failOnMedium |
Mark UNSTABLE if ≥1 Medium | false |
maxCvss |
Fail if maximum CVSS is above cutoff | 7.0 |
vinesScan(
serverUrl: 'https://vines.rosebird.org',
targetUrl: 'https://shop.example.com',
credentialsId: 'VINES_TOKEN',
preflight: true,
gates: [
failOnCritical: true,
failOnHigh: true,
failOnMedium: false,
maxCvss: 7.0
],
timeoutMinutes: 60
)
def r = vinesScan(serverUrl:'https://vines.rosebird.org',
targetUrl:'https://api.example.com',
credentialsId:'VINES_TOKEN',
preflight:true)
echo "Scan ${r.scanId} -> Crit:${r.critical} High:${r.high} MaxCVSS:${r.maxCvss}"
echo "Full report: ${r.reportUrl}"
if (r.critical > 0 || r.high > 0) { error('Risk too high') }
Gruvbox‑tinted examples you’ll see in console & reports:
parallel linux: {
node('linux') {
vinesScan(serverUrl:'https://vines.rosebird.org', targetUrl:'https://app.example.com', credentialsId:'VINES_TOKEN')
}
}, windows: {
node('windows') {
vinesScan(serverUrl:'https://vines.rosebird.org', targetUrl:'https://app.example.com', credentialsId:'VINES_TOKEN')
}
}
def r = vinesScan(serverUrl:'https://vines.rosebird.org', targetUrl:'https://app.example.com', credentialsId:'VINES_TOKEN')
if (r.critical > 0 || r.high > 0 || r.maxCvss > 7.0) {
error("Vines gate failed — Crit:${r.critical}, High:${r.high}, Max:${r.maxCvss}")
}
vinesScan(
serverUrl:'https://vines.rosebird.org',
targetUrl:'https://dev.example.com',
credentialsId:'VINES_TOKEN',
preflight:true, timeoutMinutes:90
)
- PR Smoke — quick checks, fail on critical/high only.
- Nightly Deep — full exploration, trends across builds.
- Release Barrier — strict zero critical/high +
maxCvss ≤ 7.0before publish.
Manage Jenkins → System defaults:
- Default Server URL (e.g.,
https://vines.rosebird.org) - Default Credentials (Secret text token)
- Default preflight / timeout
unclassified:
vulnerabilityVinesAi:
serverUrl: "https://vines.rosebird.org"
credentialsId: "VINES_TOKEN"
defaultPreflight: true
defaultTimeoutMinutes: 60
- Preflight failed — controller/agent cannot reach the target (DNS/port/proxy). Toggle
preflight:falsetemporarily for internal nets. - 401 from Vines — wrong/expired token; re‑create Secret text and update
credentialsId. - Gates failing builds — relax thresholds while triaging (e.g., increase
maxCvssor turn offfailOnMedium). - Not visible in “Available” — Plugin Manager → Advanced → Check now; ingestion can lag briefly after releases.
- Plugin ID:
vulnerability-vines-ai - Minimum Jenkins:
2.479.3 - Vines Cloud:
https://vines.rosebird.org - Source: jenkinsci/vulnerability-vines-ai-plugin
- Issues: GitHub Issues
- CI: ci.jenkins.io
- Release model: JEP‑229 Continuous Delivery (versions like
123.vabcdef) - Topics (GitHub):
jenkins-plugin,pipeline,security,dast,scanner,reporting,ai
Haja Mo (rocheston) — creator of Rocheston Vulnerability Vines AI.
Contributions welcome — open issues/PRs and keep docs consistent with the UI/Snippet Generator.
Apache License 2.0 © Rocheston • Designed with ❤️ by Haja Mo