OpenMFA is a Jenkins plugin that adds TOTP-based MFA for interactive logins. It introduces setup, verification, and management flows for user accounts inside Jenkins.
- TOTP MFA using authenticator apps (RFC 6238 compatible)
- QR-based enrollment flow for end users
- Global admin configuration for issuer and enforcement
- MFA user management page for administrators
- Session-based MFA verification after primary login
- Basic brute-force protection on code verification attempts
- Supports Jenkins dark theme for all UI elements
- Jenkins
2.516.3or newer
- Install the plugin from the Jenkins Plugin Manager or build it from source.
- Go to
Manage Jenkins->Security->OpenMFA Configuration. - Configure:
Issuer NameRequire MFA for all users
- Save settings.
- Ask users to enroll via the OpenMFA setup page before broad enforcement.
Showcases
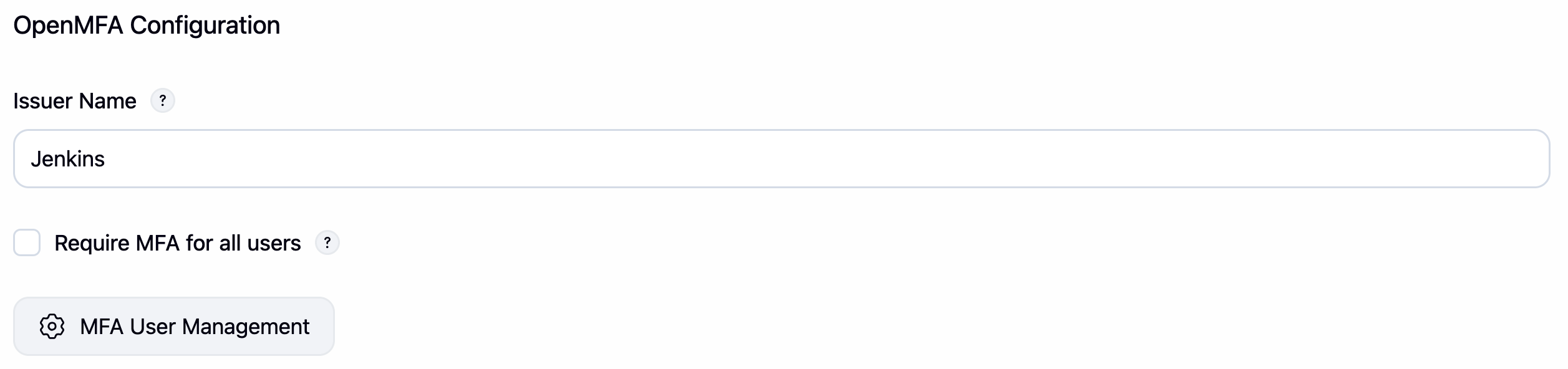 (OpenMFA Global Configuration:
(OpenMFA Global Configuration: Manage Jenkins > Security > OpenMFA Configuration)
- User signs in with username/password.
- If MFA is required and the user is not enrolled, user is redirected to MFA setup.
- User scans QR code in authenticator app and verifies setup.
- On future logins, user enters a 6-digit TOTP code.
Showcases
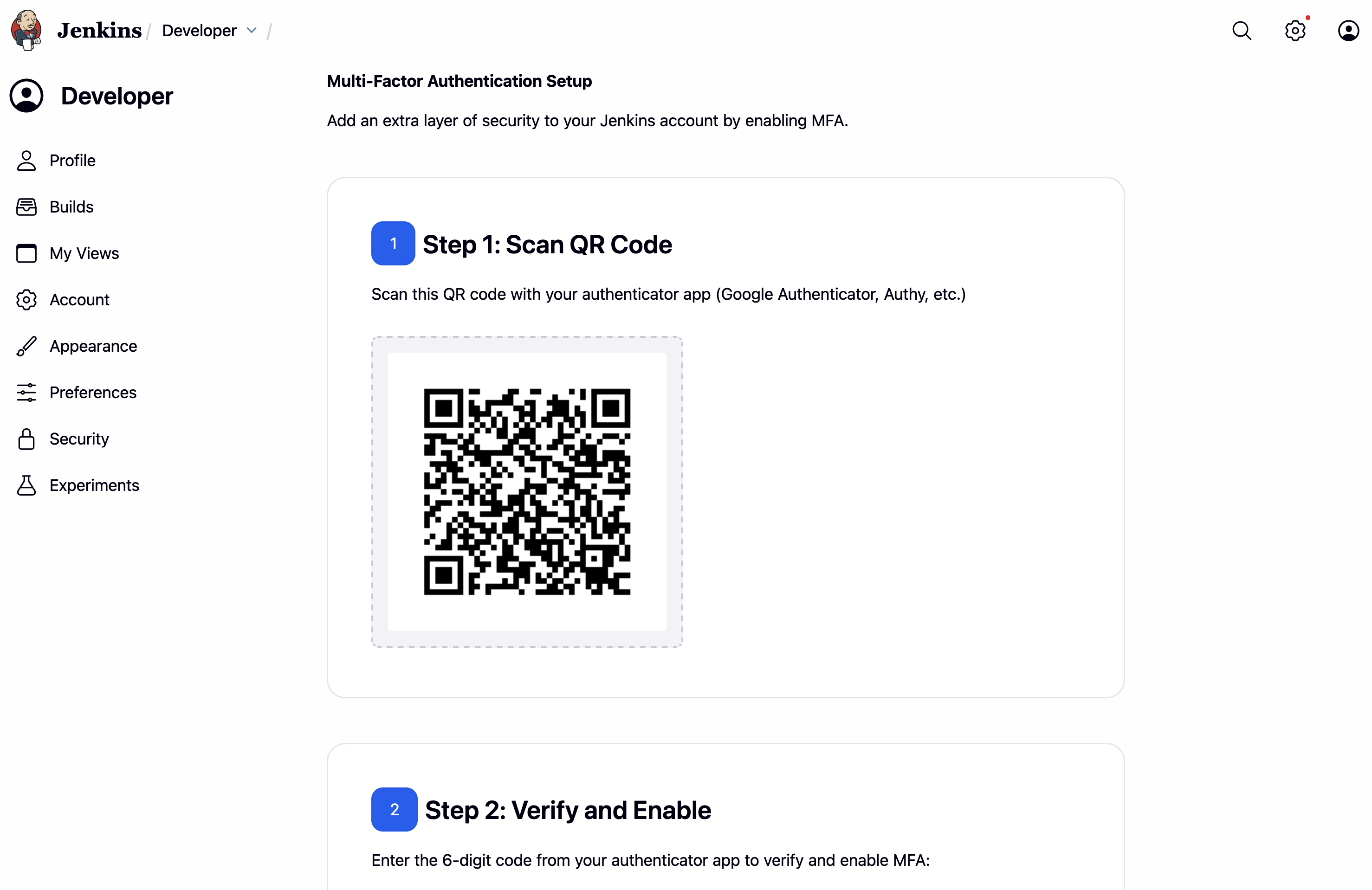 (MFA setup page:
(MFA setup page: User Property > Security > Setup MFA)
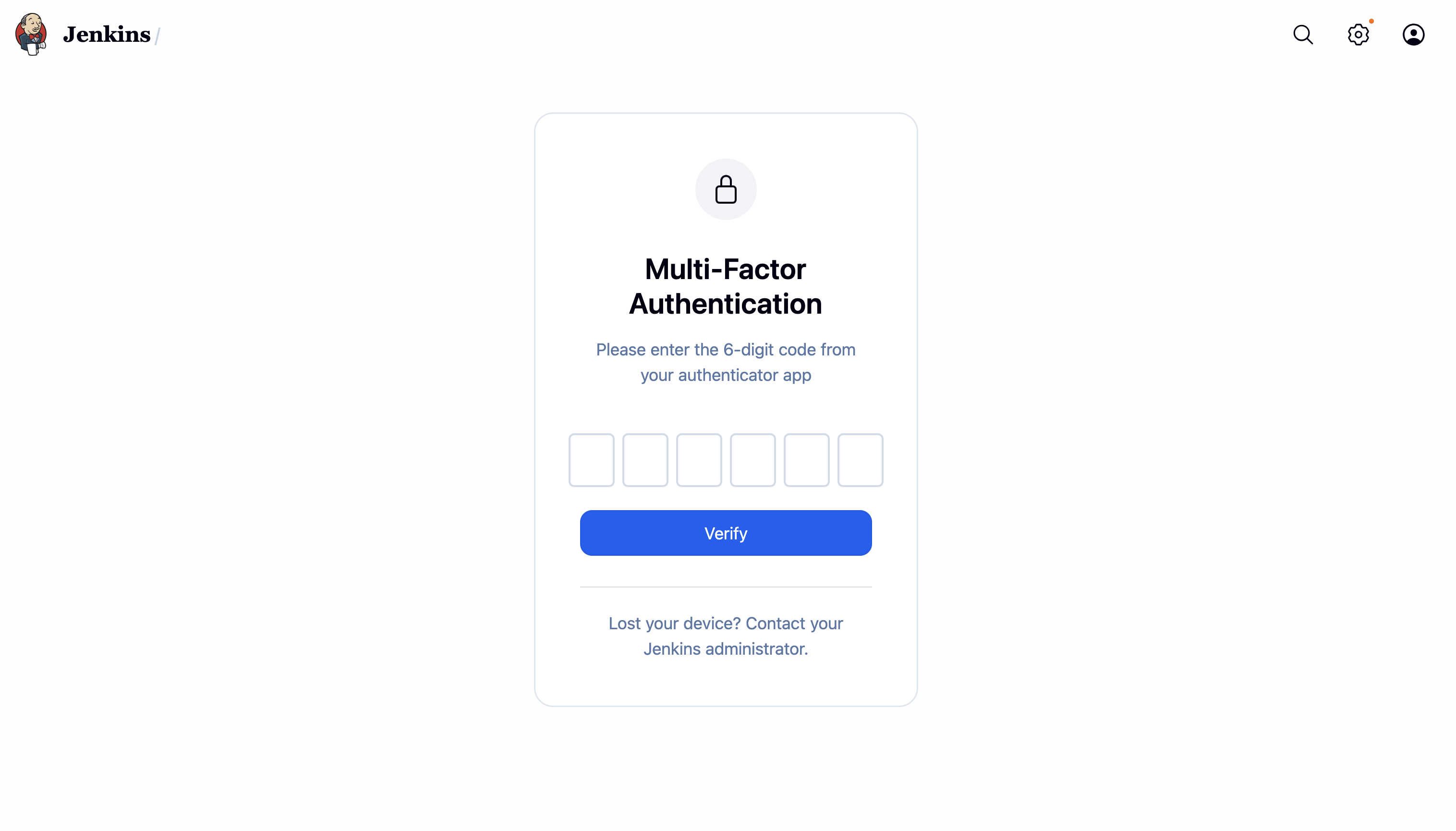 (MFA login challenge: after Jenkins
(MFA login challenge: after Jenkins login)
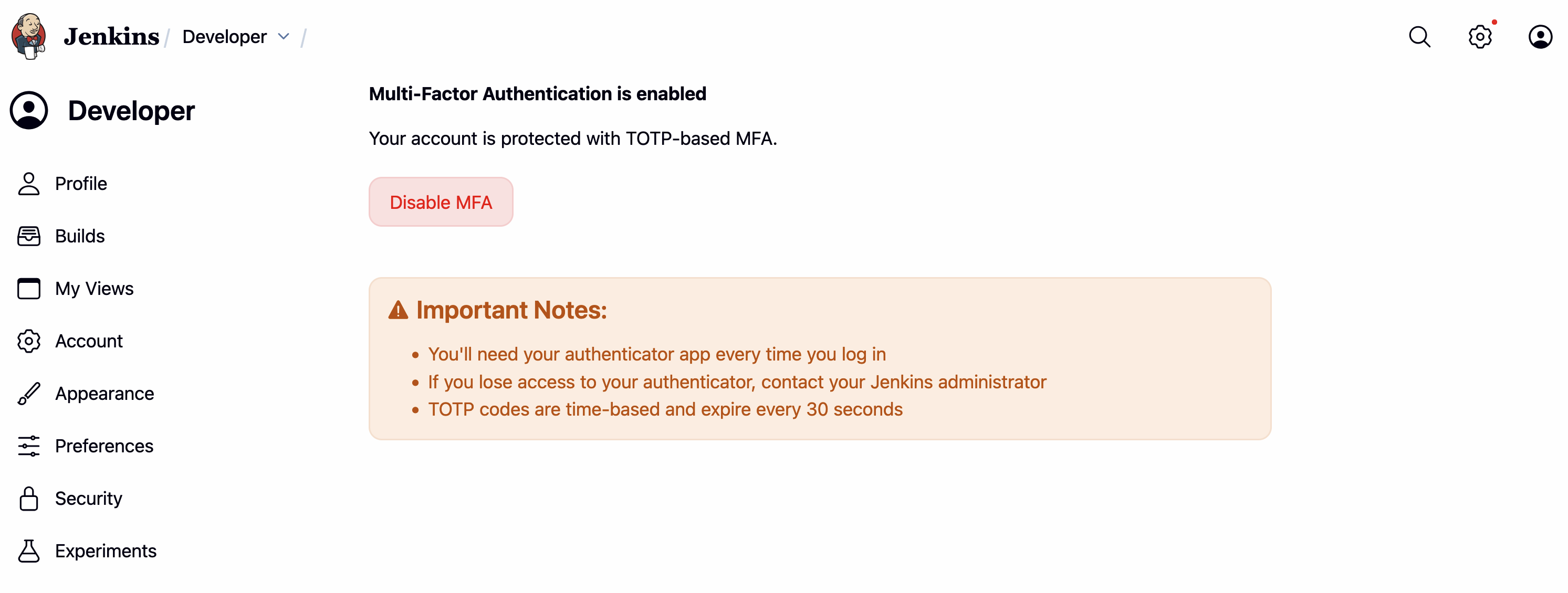 (MFA enabled:
(MFA enabled: User Property > Security > Manage MFA )
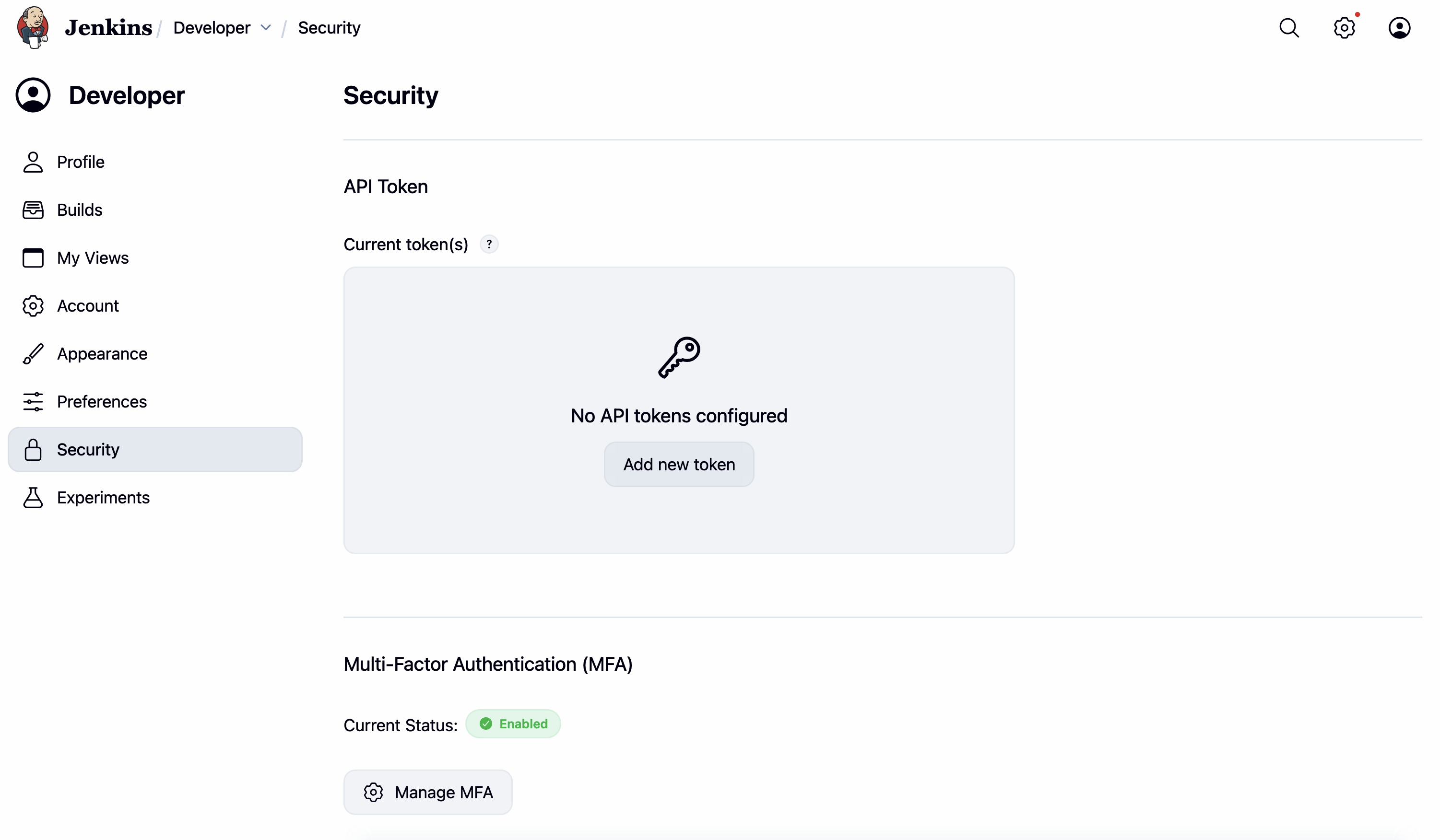 (MFA enabled:
(MFA enabled: User Property > Security)
- Go to
Manage Jenkins>MFA User Management. - Use this page to inspect enrollment state and perform admin-side MFA operations.
Showcases
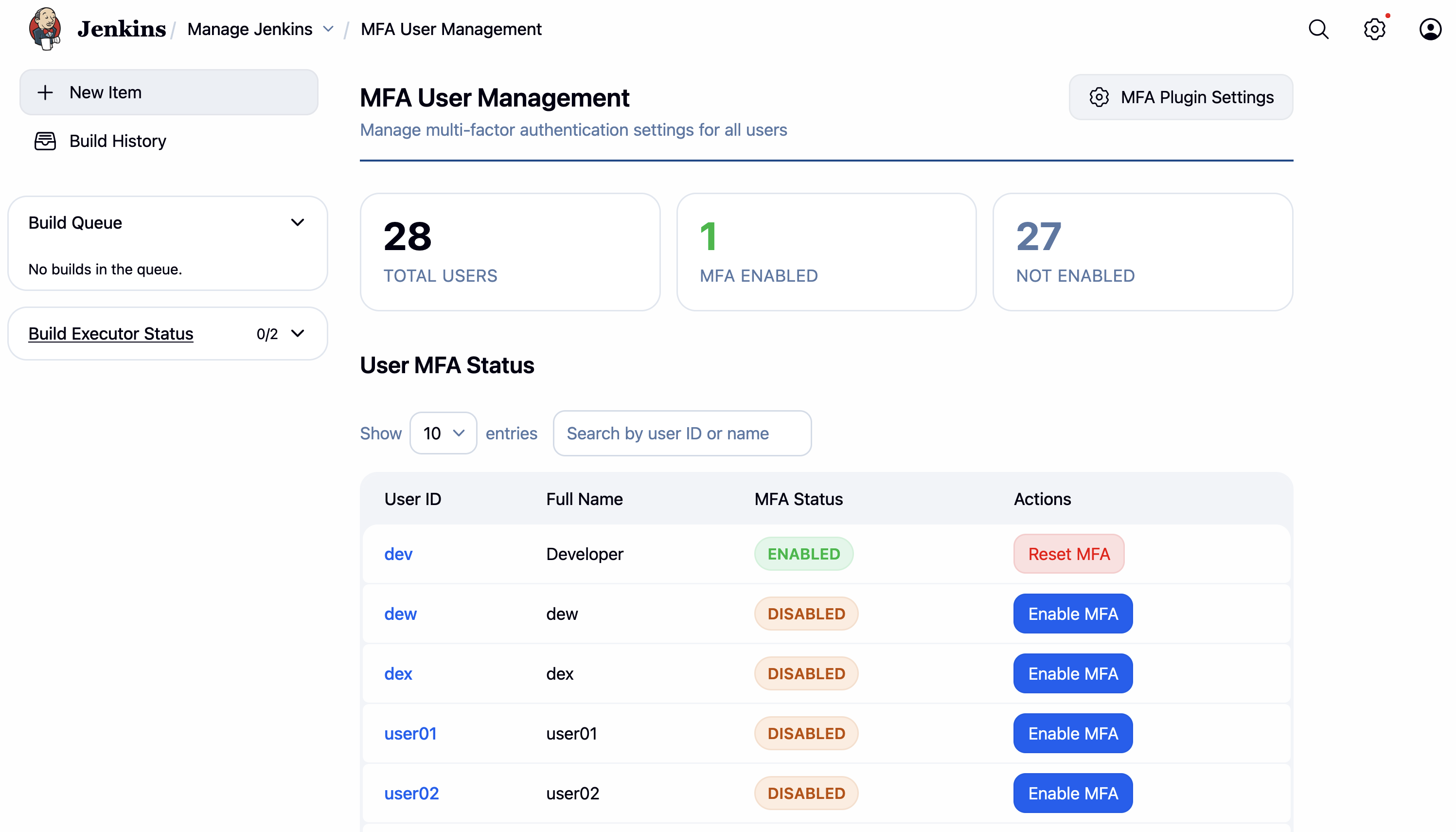 (MFA user management:
(MFA user management: Manage Jenkins > MFA User Management)
This plugin exposes global configuration and can be managed through Jenkins Configuration as Code.
Recommended workflow:
- Configure OpenMFA once from the Jenkins UI.
- Export current JCasC from your Jenkins instance.
- Copy the OpenMFA section into your managed JCasC repository.
- Apply via your standard
CASC_JENKINS_CONFIGworkflow.
Example shape (keys may vary by controller/JCasC export; use exported keys as source of truth):
unclassified:
<openmfa-global-config-key>:
issuer: 'Jenkins'
requireMFA: true
- Treat JCasC files and Jenkins configuration files as privileged, since they control authentication behavior.
- API token authentication is not challenged with interactive MFA.
- OpenMFA uses per-session verification and redirects back to the original destination after successful MFA.
The maven-hpi-plugin offers important commands for Jenkins plugin development:
-
Build and package your plugin (.hpi):
mvn install
This compiles the plugin and creates the
.hpifile (e.g.,target/openmfa-plugin.hpi), suitable for installation in Jenkins. -
Run Jenkins in development mode with your plugin:
mvn hpi:run
This starts a local Jenkins controller instance with your plugin pre-installed, typically at http://localhost:8080/jenkins/.
If you use Visual Studio Code, the repo includes a sample .vscode/launch.json for debugging Jenkins plugin development:
-
Debug Jenkins Plugin: Attaches to a Jenkins process started with
mvn hpi:runin debug mode (-Dmaven.surefire.debug), listening on port5005. -
Debug Jenkins Plugin (mvnDebug): Attaches to Jenkins launched with
mvnDebug, typically listening on port8000.
To use:
- Open this repository in VS Code.
- In VS Code, go to the "Run and Debug" panel and select a launch configuration.
You can set breakpoints in your Java code immediately.
You can configure your development environment by creating a .env file in the project root. This file is used to provide environment variables, such as JAVA_HOME, which are required for Maven or Jenkins commands.
- Sample
.envfile:JAVA_HOME=/path/to/your/java # JENKINS_HOME=/path/to/jenkins_home (optional)
How to use:
- Copy
.env.exampleto.env:cp .env.example .env
- Edit
.env, settingJAVA_HOMEto your local Java installation and any other variables as needed. - The
.envfile is automatically loaded when running development commands via the provided.vscode/run.sh(used invscode/tasks.json) script, ensuring your environment variables (likeJAVA_HOME) are available.
Tip: .env is ignored by git, so your local secrets and paths are not committed. Use .env.example as a starting point for other developers.
This project uses Spotless with Eclipse formatter rules from fmt.xml. It also ships a prek config in .pre-commit-config.yaml.
-
Install git hooks with
prek:prek install
-
Run all configured checks/formatters with
prek:prek run --all-files
-
Check formatting:
mvn spotless:check
-
Apply formatting:
mvn spotless:apply
Spotless checks are also executed during Maven compile, so formatting issues fail the build.
MIT. See LICENSE.md.





