Google Analyze Code Security
The Google Analyze Code Security plugin for Jenkins identifies insecure configurations in Infrastructure as Code (IaC) files for Google Cloud resources. This plugin requires Terraform plan files in JSON format for scanning.
Note: Don’t enter any sensitive information such as passwords and other personal identifiable information in the Terraform plan files.
Set up credentials
Service Account Based Credential
- In the Google Cloud organization which includes the resources that you want to change, create a service account.
- Add the
Security Posture Adminrole or theSecurity Posture Shift-Left Validatorrole to the service account. - Create the service account key in JSON format and download the JSON file.
Configure the plugin
- In the Jenkins console, click
Manage Jenkins>Configure System. - In the Google Analyze Code Security section, click Add to add the service account key.
- Add the service account key.
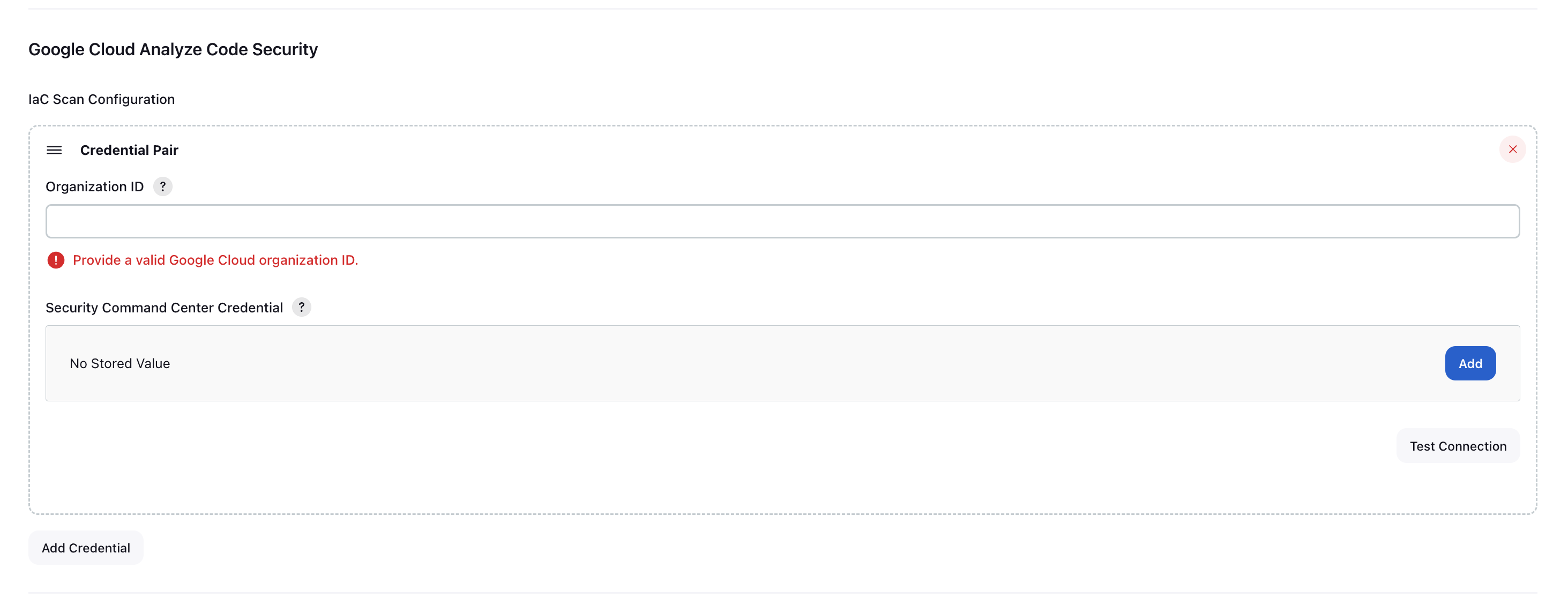
OrganizationId: Enter the organization ID for the Google Cloud organization that includes the resources.SCC Credentials: Add the service account key.
- [Optional] To validate the credentials, click Test Connection.
- To add additional service account keys, click Add.
- Click Save.
Add the plugin to your build project
- In the Jenkins console, click Corresponding Project > Configuration.
- Click Add build step > Perform Code Scan during Build.
- Complete the following fields:
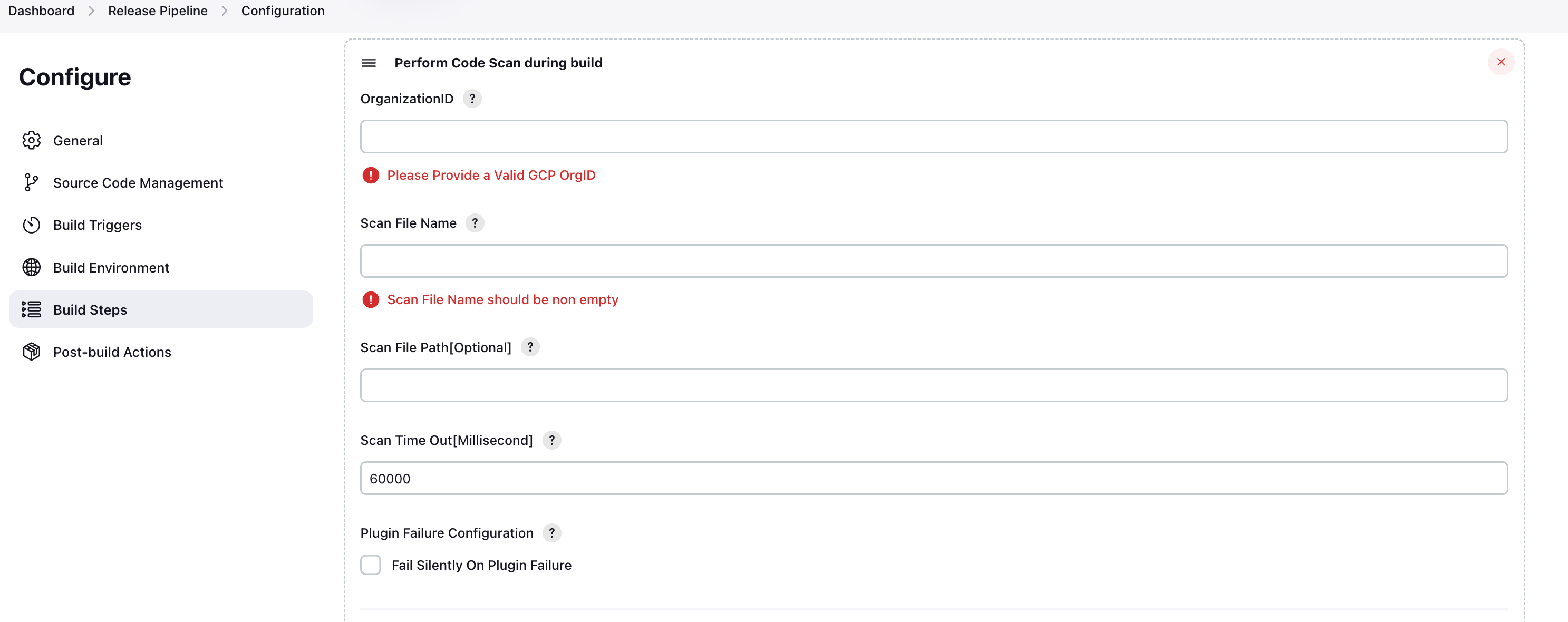
- OrganizationID: The Google Cloud organization ID.
- Scan File Name: The name of the Terraform plan file (in JSON format) that you want to scan. The plugin scans the workspace directory and its subdirectories for the file, if you don’t enter a {Scan File Path}.
- Scan File Path [Optional]: The path to the JSON plan file, relative to the project workspace directory. For example, if the file is located in
/xyz/abc/myplanfile.json, the file path is/xyz/abc. - Scan Time Out[Millisecond]: The time after which the plugin stops and changes the build status to failure.
- Plugin Failure Configuration: Determines build status when the plugin runs into an error. If you set this field to
true, the build status is marked asSUCCESS. Otherwise, if you set this field tofalse, the build status is marked asFAILED.
- Complete one of the following actions to determine how a build proceeds:
- To configure a build to fail depending on how many issues are found, complete the following:
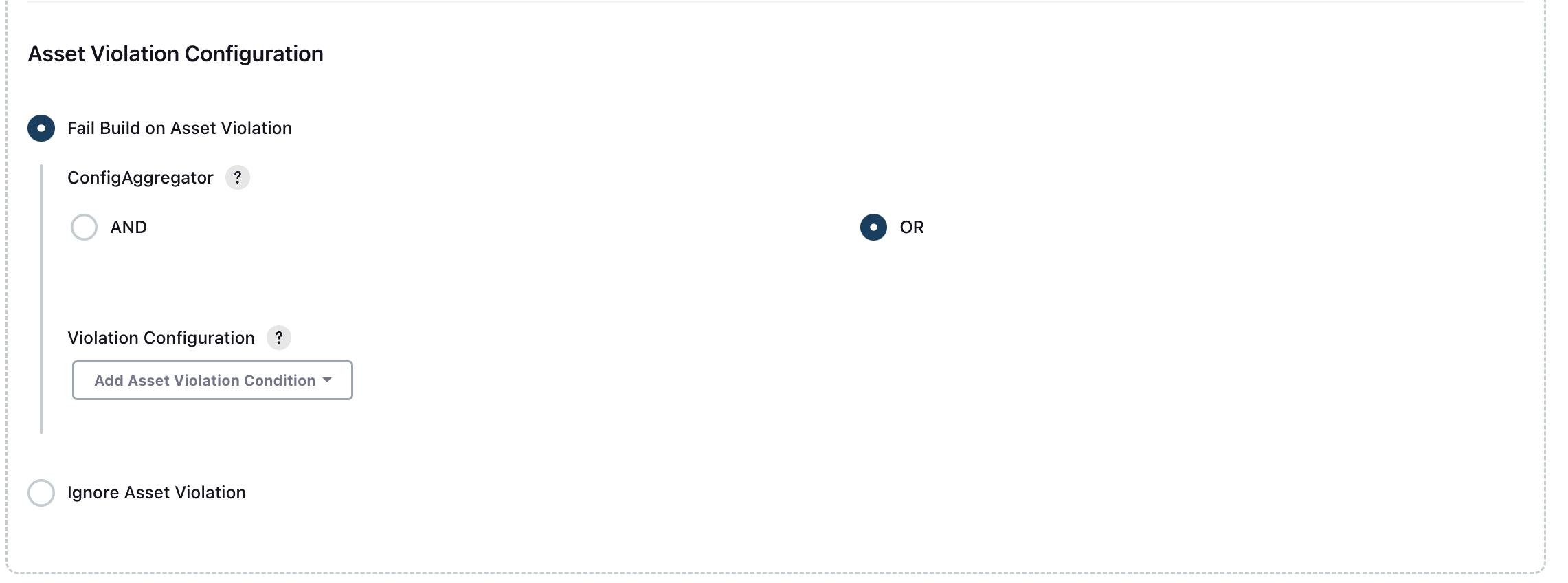
- Click
Add Asset Violation Config. - Select a severity class and enter a corresponding violation count threshold.
- Select the aggregator value (either OR or AND).
Sample Configuration:
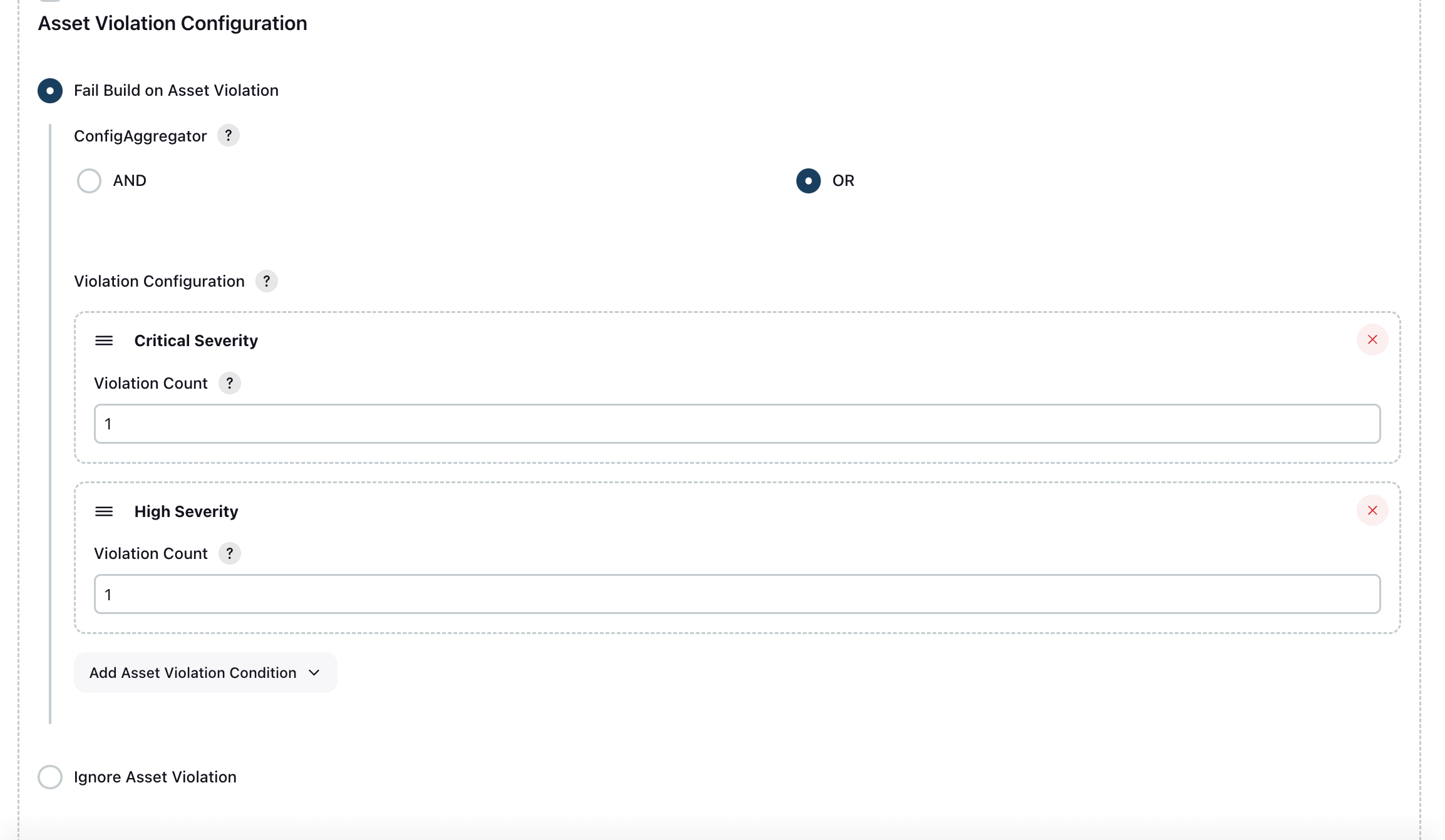
- Click
- To configure a build to finish, regardless of the number of issues found, select Ignore violations reported in the Code Scan while evaluating build Status.

- To configure a build to fail depending on how many issues are found, complete the following:
- Click Save.
- To run the project, click Build Now.
- To view the plugin report, click the most recent workflow.
- If the plugin ran, it publishes a violation report under Build Artifacts.
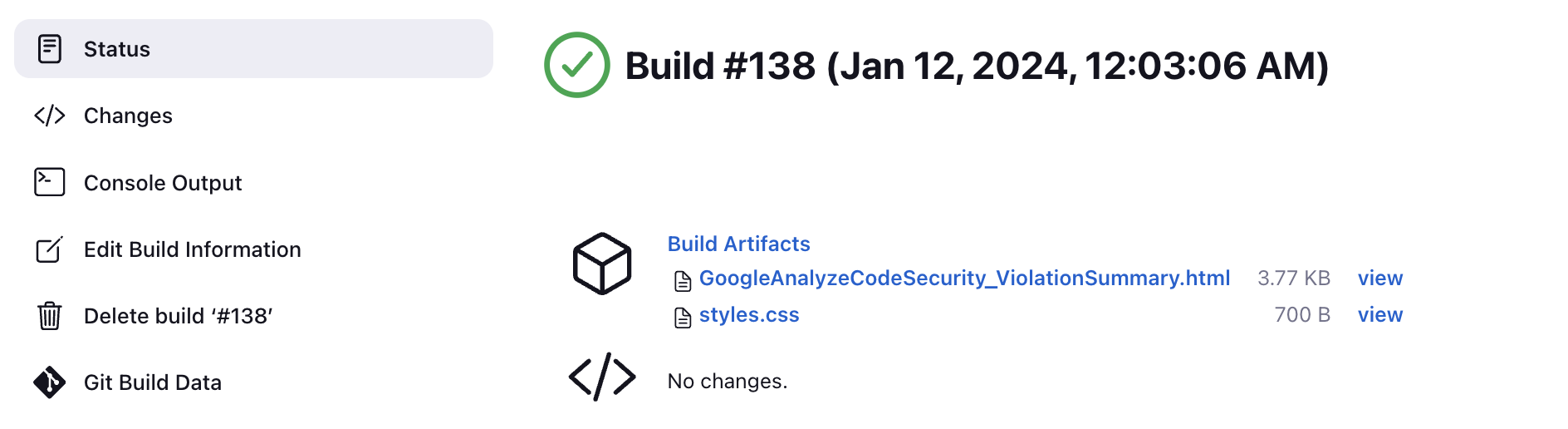
- If the plugin failed, it publishes an error report under Build Artifacts.
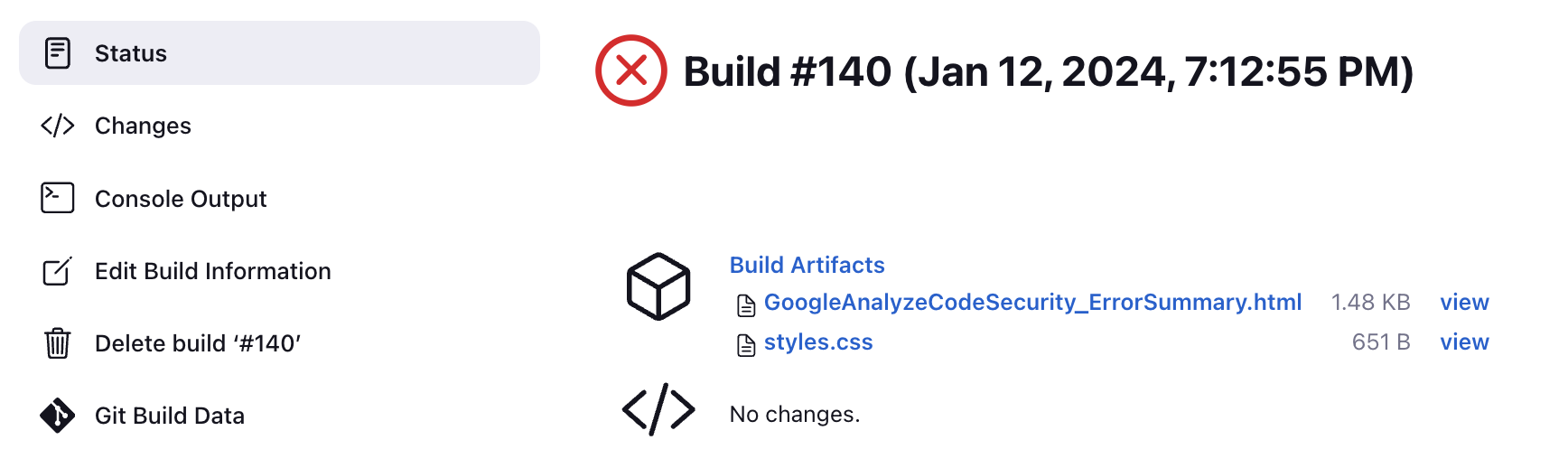
- If the plugin ran, it publishes a violation report under Build Artifacts.
Supported asset types and policies
For information about supported asset types and policies, see IaC Validation - Supported assets and policies.