This plugin enables below features for Credentials,
- Credential Access Filtering
- Credential Usage Reporting
This feature enables defining rules for allowing/blocking access to the credentials from the Projects/Jobs/Items.
When a credential is accessed by a Project/Job/Item, this plugin interferes and follow the below logic,
- Loops in all the Credential Rule Definitions
- Checks if the ID of the credential, which is being accessed, matches with the
credentialPatternvalue of any rule.- If there is match, checks if the Project/Job/Item name matches with the
itemPatternvalue of the rule which has matched on the previous step.- If there is match, returns True to the controller method where credential access is allowed.
- If there is no match, return False to the controller method where credential access is blocked.
- If there is no match, allows/blocks access depending on the Default Restriction Mode
- If there is match, checks if the Project/Job/Item name matches with the
Credential Rule has three properties which must be set during the definition.
Rule Name: Name of the rule. Credential Pattern: Regex Pattern for Credentials. Item Pattern: Regex Pattern for Project/Jobs/Items.
Plugin has a default behavior setting which decides on allowing/blocking access to the credentials if there are any matches or not.
-
Restrict access if a credential is not matched with one of the defined patternsRestrict access to a credential if the credential ID does not match with any of the defined rules. With this behaviour all access to all credentials will be blocked unless a defined rule matches.
-
Do not restrict access if a credential is not matched with one of the defined patternsAllow access to the credential if the credential does not match with any of the defined rules. With this behaviour access will be blocked only for the credentials which matching with a rule.
For defining Credential Access Rules please follow the below steps
-
Navigate to "Manage Credential Rules" section under "Manage Jenkins" as shown below
-
Set the default Restriction Mode as shown below
-
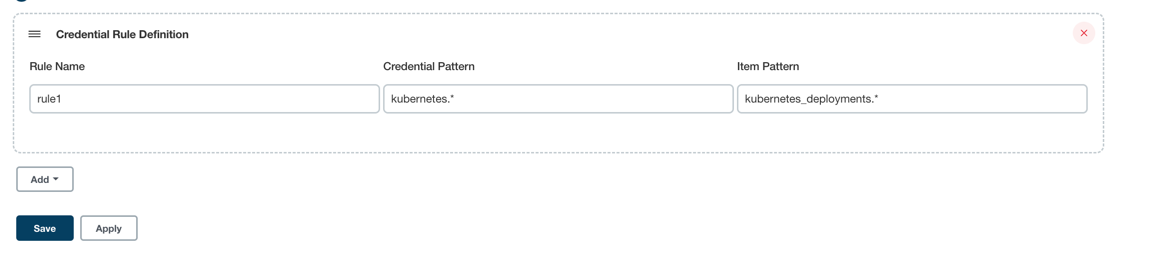
Define rules as many as you need. An example definition is shown below
-
Save your changes.
Credential Rule definitions can be defined by using Jenkins Configuration as Code approach.
You can use the below definition on the root level of the Jenkins CASC file.
credentialRules:
restrictNotMatching: true/false
<Rule Name 1>:
credentialPattern: "<Regex Pattern>"
itemPattern: "<Regex Pattern>"
<Rule Name 2>:
credentialPattern: "<Regex Pattern>"
itemPattern: "<Regex Pattern>"
An example definition can be found below,
credentialRules:
restrictNotMatching: true
rule1:
credentialPattern: "kubernetes.*"
itemPattern: "kubernetes_deployments.*"
This feature enables reporting Credential Usage with the below details,
- Total Usage Count: Total number of accesses for each credential.
- Project/Job/Item Usage Count: Total number of credential access grouped by Project/Job/Item.
- Node Usage Count: Total number of credential access grouped by Nodes.
For accessing usage report please follow the below steps