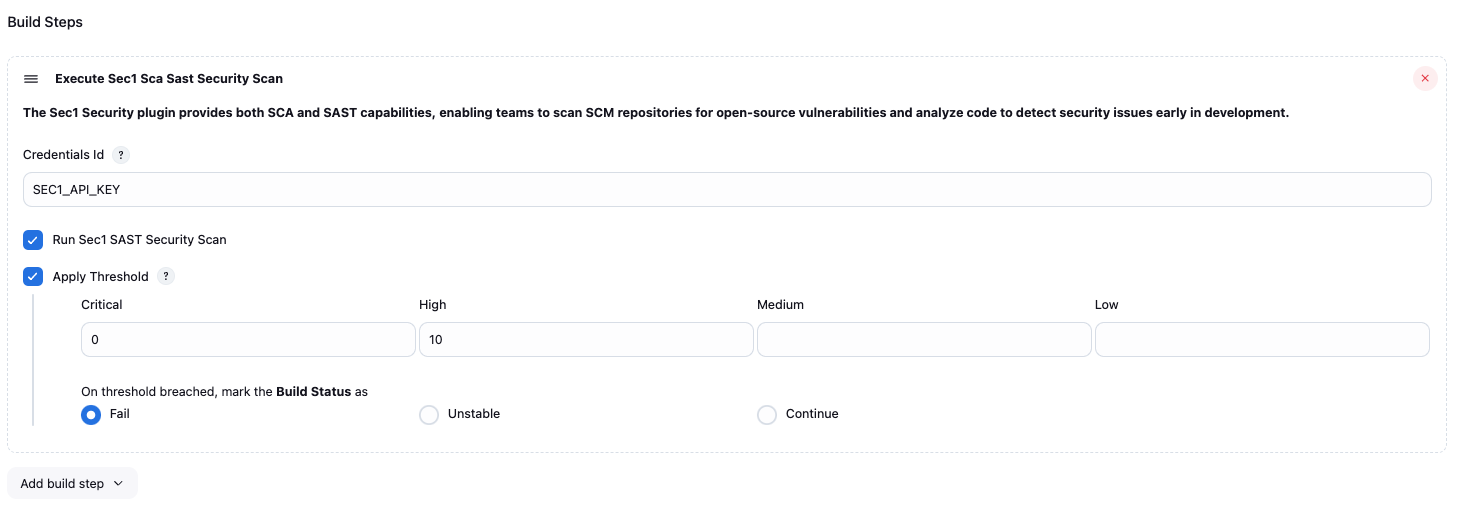
The Sec1 Security plugin provides both SCA and SAST capabilities, enabling teams to scan SCM repositories for open-source vulnerabilities and analyze code to detect security issues early in development.
To use the plugin up you will need to take the following steps in order:
- Install the Sec1 Security Plugin
- Configure a Sec1 API Token Credential
- Add Sec1 Security to your Project
- Go to "Manage Jenkins" > "System Configuration" > "Plugins".
- Search for "Sec1 Security Scanner" under "Available plugins".
- Install the plugin.
By default, Sec1 uses the https://api.sec1.io endpoint. It is possible to configure Sec1 to use a different endpoint by changing the SEC1_INSTANCE_URL environment variable:
- Go to "Manage Jenkins" > "System Configuration" -> "System"
- Under "Global properties" check the "Environment variables" option
- Click "Add"
- Set the name to
SEC1_INSTANCE_URLand the value to the custom endpoint
- Go to "Manage Jenkins" > "Security" > "Credentials"
- Choose a Store
- Choose a Domain
- Go to "Add Credentials"
- Select "Secret text"
- Add
<YOUR_SEC1_API_KEY_ID>as ID and Configure the Credentials. - Remember the "ID" as you'll need it when configuring the build step.
To get Sec1 Api Key navigate to My Account > "Login with GitHub" > Click on profile icon at top right > "Settings"
- In "API key" section, click on "Generate API key"
- Copy key for use.
This step will depend on if you're using Freestyle Projects or Pipeline Projects.
- Select a project
- Go to "Configure"
- Under "Build", select "Add build step" select "Execute Sec1 Security Scanner"
- Configure as needed. Click the "?" icons for more information about each option.
Use the sec1Security step as part of your pipeline script. You can use the "Snippet Generator" to generate the code from a web form and copy it into your pipeline.
Whether the step should fail if issues and vulnerabilities are found. You can pass the following parameters to your `sec1Security` step.📷 Show Example
pipeline { agent any stages { stage('Build') { steps { echo 'Building...' } } stage('Sec1 Sca Sast Security Scan') { steps { script { sec1ScaSastSecurity ( scanFileLocation: "${WORKSPACE}", // this is the location of you scm checkout directory. if not configured don't change it. apiCredentialsId: "<Your Sec1 Api Key ID>", //optional runSec1SastSecurity: true, applyThreshold: true, actionOnThresholdBreached: "unstable", threshold: [criticalThreshold: '0', highThreshold: '0'] ) } } } stage('Deploy') { steps { echo 'Deploying...' } } } }
Location where scm checkout is done. Default is ${WORKSPACE} of build job.
Scan will fill if you dont provide this value.
Sec1 Api Key Credential ID. As configured in "2. Configure a Sec1 API Token Credential".
Whether SAST scanner needs to be executed for configured git repository
Whether vulnerability threshold needs to be applied on the build.
Threshold values for each type of vulerability. e.g. configuration: [criticalThreshold: '0', highThreshold: '10', mediumThreshold: '0', lowThreshold: '0']
If scan reports gives more vulnerabilities than configured threshold for the respective type of vulnerability then error will be shown in console and build status will be modified based on actionOnThresholdBreached value.
The action which needs to be taken on build if vulnerability threshold is breached. Possible values: fail, unstable, continue
To see more information on your steps:
- View the "Console Output" for a specific build.
-- Sec1 team