A Jenkins plugin that implements OIDC Backchannel Logout support for any compliant OpenID Connect (OIDC) Identity Provider.
This plugin bridges the gap between your OIDC Identity Provider and Jenkins by ensuring that when a user logs out from the IdP (or when their session is terminated via the IdP's admin console), their session in Jenkins is immediately invalidated.
- Session Mapping: Automatically tracks the relationship between OIDC Session IDs (
sid) and Jenkins HTTP Sessions upon login. - Backchannel Endpoint: Exposes a secure, unauthenticated endpoint to receive Logout Tokens from your OIDC provider.
- Instant Termination: Parses JWT Logout Tokens, validates them, and invalidates the active Jenkins session without requiring user interaction.
To use this plugin, you must have the following installed and configured:
- Jenkins (Version 2.492.3 or newer recommended).
- OpenId Connect Authentication Plugin (
oic-auth) installed and configured as the Security Realm.- Note: This plugin relies on
oic-authto handle the OIDC Core Features.
- Note: This plugin relies on
You need to configure your OIDC Identity Provider to send backchannel logout requests to Jenkins.
- Log in to your OIDC provider's admin console.
- Navigate to the client/application representing Jenkins.
- Locate the Backchannel Logout URL or equivalent field.
- Enter the URL in the following format:
https://<YOUR_JENKINS_URL>/oidc/backchannel-logout - Save the configuration.
-
Login: When a user logs in via OIDC, this plugin's
SessionListenercaptures thesid(Session ID) from the ID Token and maps it to the current JenkinsHttpSessionin memory. -
Logout Event: When a logout occurs in your OIDC provider (e.g., user signs out or an admin terminates the session), the provider sends a
POSTrequest with a signed JWT (logout_token) to the URL configured above. -
Invalidation: The plugin validates the token, extracts the
sid, looks up the corresponding Jenkins session, and callssession.invalidate(). The next time the user tries to click a link in Jenkins, they will be redirected to the login page.
This demo below uses Keycloak as an example OIDC Identity Provider. 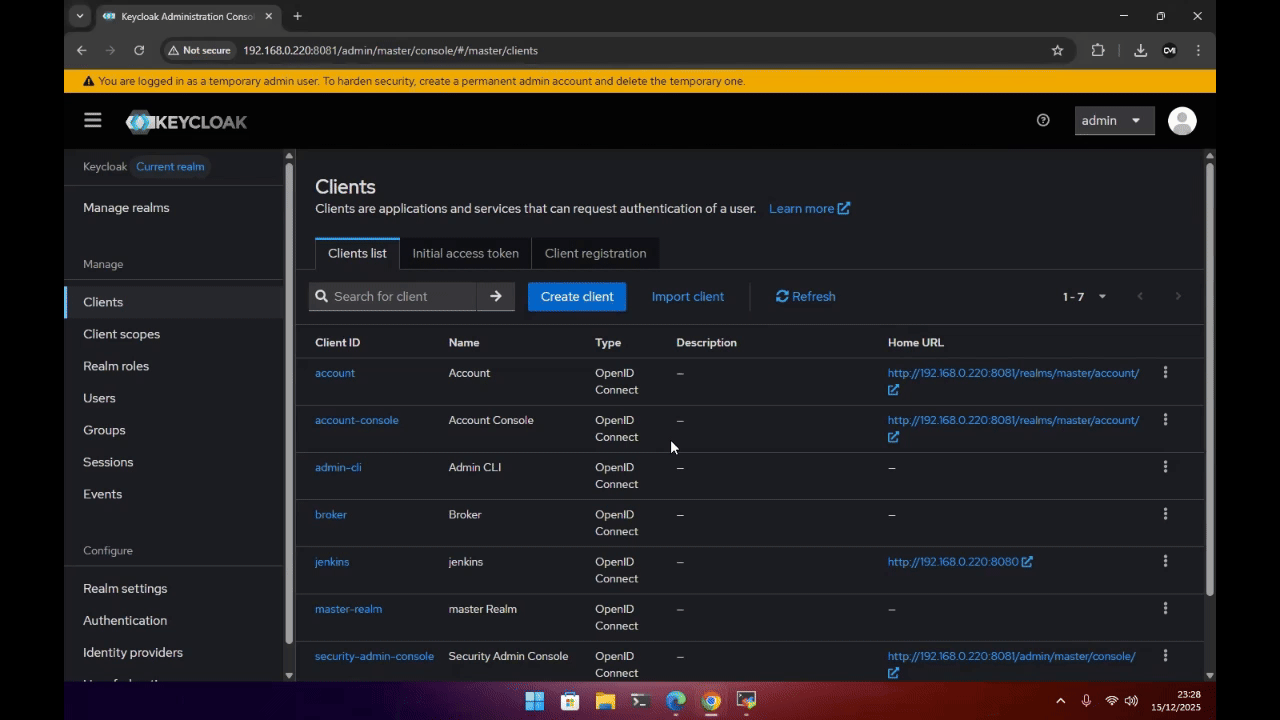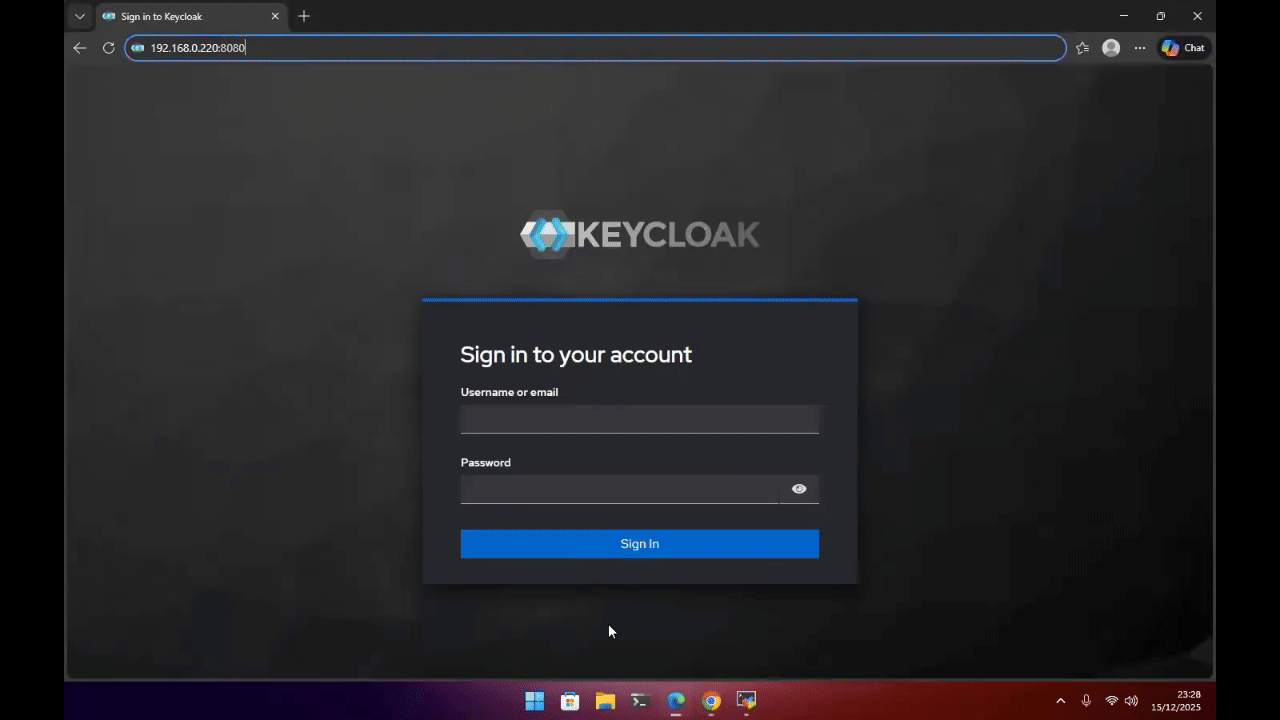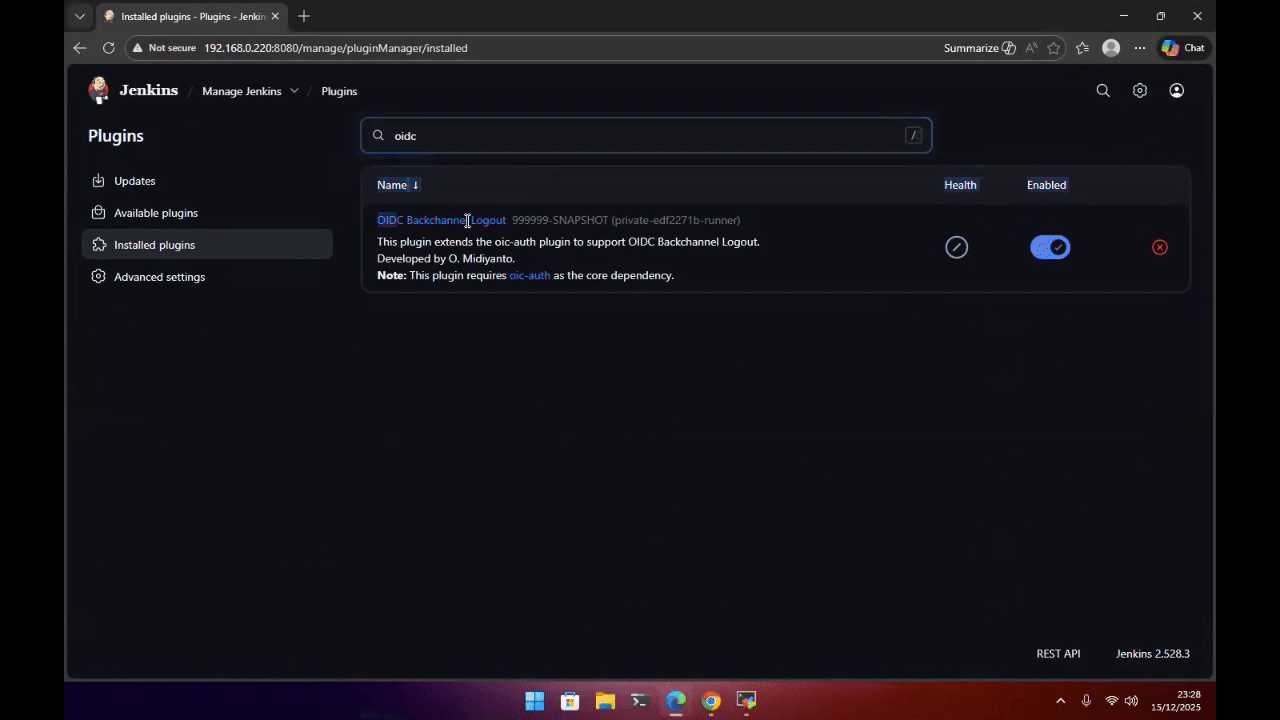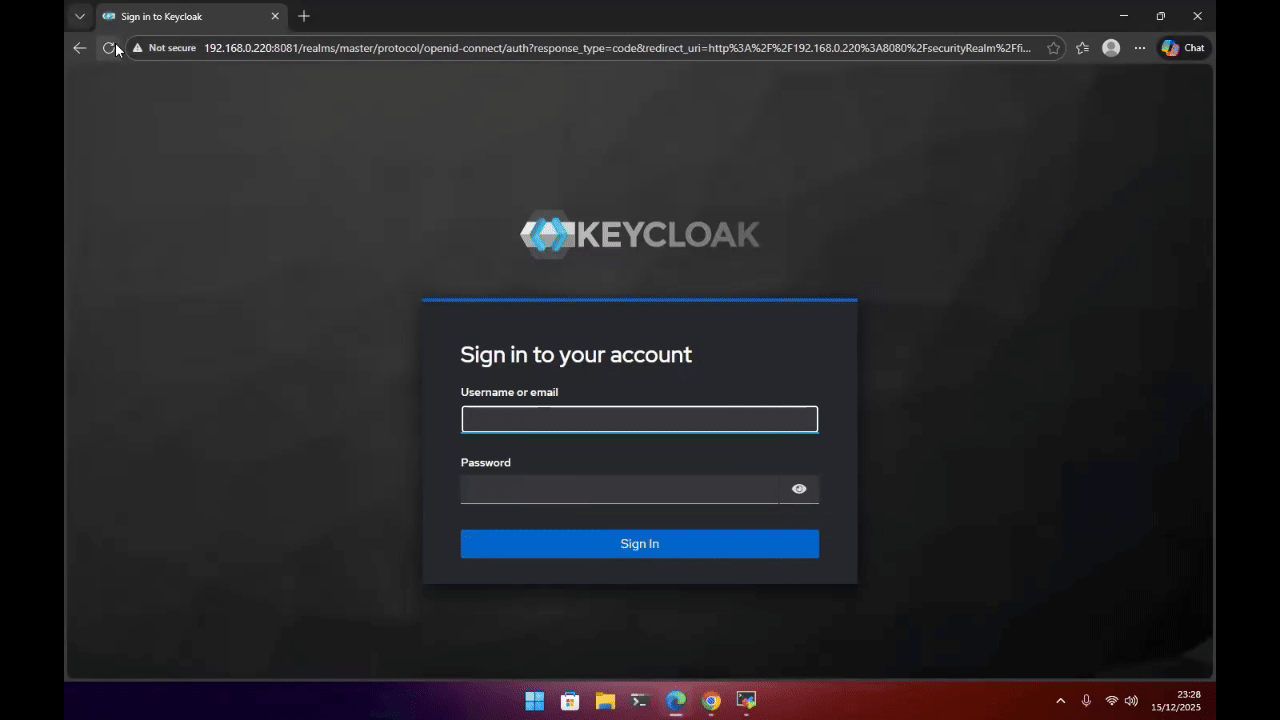
SessionTracker is in-memory only: This plugin uses an in-memory map to track the relationship between OIDC session IDs (sid) and Jenkins HTTP sessions. As a result, it does not support High Availability (HA) or clustered Jenkins environments (such as CloudBees CI HA) where multiple controller instances are used. Session mappings will not be shared across nodes, so backchannel logout may not work reliably in these scenarios.
Contributions are welcome! Please submit a Pull Request or open an issue if you encounter any bugs.
This project is licensed under the MIT License - see the LICENSE.md file for details.